GootLoader is malware that has been actively used by attackers to deliver additional malware to undermined devices. According to the reports of Cyberreason, The updates in GootLoader have resulted in several fluctuations of the malware, with Gootloader 3 currently in active use. Despite the updates in the elements the overall functionality and strategy remain similar to its early activity in 2020.
GootLoader being a part of the Gootkit banking trojan is a malware downloader. It is closely related to the Hive0127 group AKA UNC2565. To download post-exploitation tools Javascript is used by this malware which is distributed by using the SEO poisoning method.
Gootloader is often used to deliver various malware such as Cobalt Strike, Gootkit, IcedID, Kronos, REvil, and SystemBC. A few months ago, the attackers behind GootLoader released their own order and control and lateral movement tool called GootBot. Furthermore implying that they are extending their operations for greater monetary gain.
Malicious GootLoader JavaScript
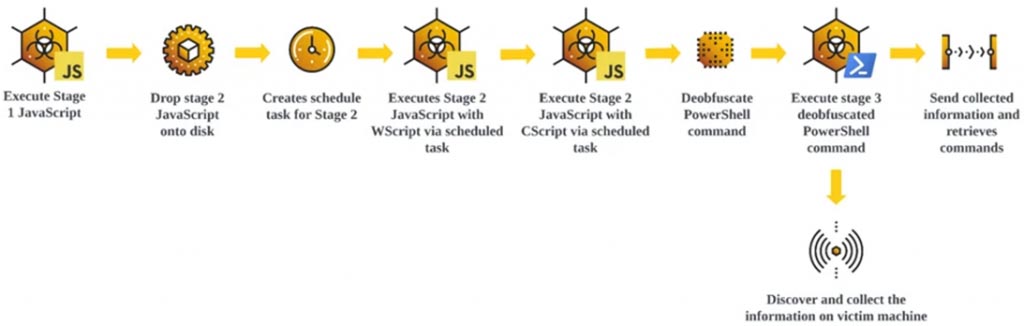
Attack chains include compromising websites to host malicious GootLoader JavaScript code masked as legitimate documents and agreements. When such files are executed, a prepared task is created in Windows to maintain the persistence of the infection. An additional PowerShell script is executed to gather information about the system and await further instructions.
Security researchers from Cybereason have highlighted that malicious websites hosting archive files for infecting users are employing SEO tactics to lure victims searching for business-related files like contract templates or legal documents.
These attacks are further distinguished by their adoption of techniques such as source code encoding, obfuscation of control flows, and increasing payload sizes to hinder detection and analysis. Another notable method involves embedding malware within legitimate JavaScript library files such as jQuery, Lodash, Maplace.js, and tui-chart.
According to the researchers, recent updates to GootLoader have enhanced its stealth and evasion capabilities. Significantly amplifying its threat level compared to previous repeated thefts. To defend against such cyber threats, it is crucial to consistently update software. Furthermore, utilize trusted antivirus solutions, and exercise caution when handling files from sources that are not fully trusted.
Source: SecurityLab Ru




